CyLock PKI
Identity theft and data breaches are increasing day by day. The root cause to this problem is in using weak passwords which makes the single-factor method of authentication no longer a sufficient security control. Two-factor authentication is now essential to protect user identity and enterprise data.
Cybernexa’s CyLock PKI platform is a secured Public Key Infrastructure (PKI) based solution that provides strong certificate-based two factor authentication for the protection of user identity and enterprise data and applications. It can be used for enabling two-factor authentication during network logon, online transactions and workflows. It relies on asymmetric authentication where a pair of encryption keys — namely, a private key and a public key is used to carry out authentication.
Certificate based two factor authentication is made possible using USB tokens or Smart Cards, which securely store the private keys. These hardware devices ensure that the private key never leaves the devices. Our platform provides comprehensive security controls to certificate issuance thereby enabling strong two-factor authentication with non-repudiation, and integrity for each transactions / workflow processes.
Why PKI USB Tokens or Smart cards?
-
Tamper-resistant storage that protects private keys and other personal identity information
-
Isolation of security-critical functions that facilitate authentication, digital signatures, and key exchange
-
Private Keys never leave the device, all computations are performed on the device
-
Portability of USB tokens across computers / laptops
-
Authentication using a PKI USB token or smart card requires the user to enter a PIN known only to them. This PIN together with the physical device containing the user’s digital identity provides a strong two-factor authentication
CyLock PKI for Secure Banking
The Reserve Bank of India (RBI) has directed banks to introduce PKI-based system for authentication and transaction verification in online banking transaction to ensure transactions security, due to the increasing frauds happening in online banking sector.
For banks, CyLock PKI platform provides a Digital Signature Certificate (DSC) based second-factor authentication mechanism to ensure authenticity, non-repudiation, confidentiality and integrity of the data transmitted during online banking. DSC can be used to prove your identity, to access information or services on the Internet or to sign certain documents digitally.
How DSC works for Online Banking?
Users can buy USB PKI Tokens supplied be various Certifying Authorities or Registration Authorities across India. After that they have procured the tokens, they can buy Class III certificate from RAs online and load the certificate securely into the USB PKI token. The token can be secured by providing a PIN during the loading of the certificate into the token device. This is to ensure that the private key never leaves the device and cannot be read without the PIN.
Registration Process:
The first step is to register their device and DSC with the online service portal. After entering the required fields, insert the DSC USB token to send the public key to the online service portal for associating it with the user’s account. After successful registration user can authenticate themselves during application login or transactions using the USB token.
Login / Transaction Process:
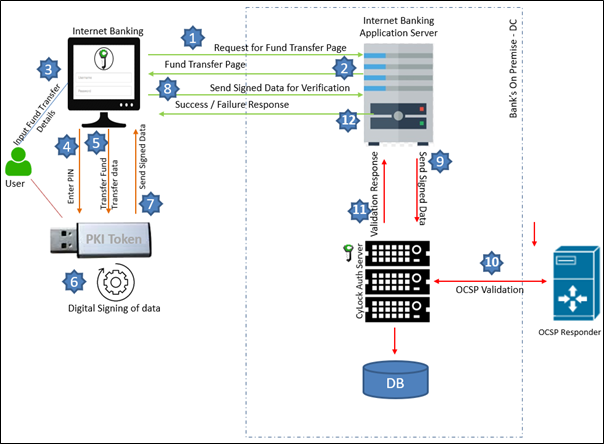
During application login or online transactions, user needs to authenticate using the client USB device to prove possession of the private key / DSC. The private key can only be used after successfully authenticating by entering the PIN. With the user account identifier provided by the service, the device selects the correct key and cryptographically signs the request challenge. The signed challenge is sent to the calling service, which is verified with the stored public key and allows the user to login. The online transaction (fund transfer) authentication process using PKI USB device is given below.
-
User accesses fund transfer page
-
Fund transfer page displayed in user’s browser
-
User enters the fund transfer details in Online Internet banking portal
-
These details are sent to the PKI USB token connected to the local PC or laptop through USB
-
User is prompted for PIN to login to the token device
-
Using the identified DSC, the transaction details are signed using the private key
-
Token device sends the signed transaction details to the calling service
-
Along with other details signed data is sent to Internet Banking Application Server
-
Internet Banking Application Server sends the signed data to CyLock Auth Server for validating the digital signature
-
CyLock Auth server sends the OCSP request to verify the certificate authenticity
-
Authentication server verifies the digital signature using the public key of the user and the transaction data. Success / failure response is to Internet Banking Application Sever
-
Based on the response from CyLock Auth server, fund transfer is approved or rejected by the Internet Banking Application Server
CyLock PKI for Network Logon
Most of the systems require simple password-based authentication to allow access and provide total control of the system. But passwords are also the weakest as there are a wide variety of attacks such as brute force attacks, eavesdropping, and social engineering tactics using which attackers can gain / acquire user credentials and impersonate their identity.
Smart cards or PKI USB tokens offer a more secure means of authentication than a traditional password-based logon. It provides greater security as the user should possess the physical Smart card or the PKI token and also know the PIN that provides the access to the device to carry out authentication during network logon.
How PKI USB token works for Windows Network Logon?
Organizations having Microsoft Active Directory Server can use the Active Directory Certificate Services (ADCS) that is part of the server components to create a Public Key Infrastructure for internal use. After setting up the ADCS, digital certificates can be issued to each network logon user who are member of Active Directory.
User Enrollment
The first step is to set up Enrollment stations to issues digital certificates to the network logon users or desktops. The “smart card logon template” is restricted to administrators by default. Set the extended permissions on the template to enable common users to request certificates. Enrollment certificate should be issued that will allow the administrator to request certificate on behalf of other users. For each user connect the PKI USB token or Smart Card into the system and request a ‘User Certificate’. This will create a unique key pair and install the certificate in the token. Secure the token by giving a PIN while the certificate is installed.
PKI USB Token / Smart Card Logon:
-
Attach the USB security token to the computer or insert the smart card to the card reader
-
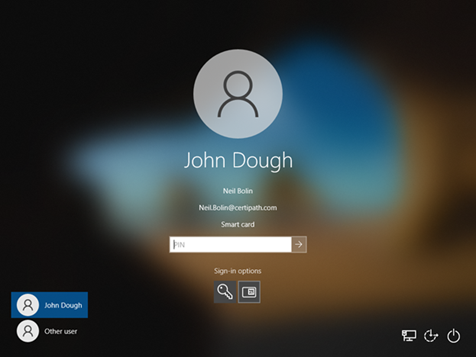
Choose the Smart card tile displayed on the logon screen (see screenshot below).
-
The identity of the user logging in is obtained automatically from the certificate presented by the smart card or PKI USB token
-
System will prompt for PIN. Enter the PIN as set
-
If the PIN is correct user details and other information will be digitally signed and submitted to the KDC service, running in the domain controller
-
If the digitally signed data is valid the user will be allowed to logon to the network
Platform Components
-
CA Server
-
CyLock Portal
-
Client Components for digitally signing Transactions / Data
-
Certificates
-
PKI USB Token or Smart Cards
-
Eliminate the need to manage multiple passwords thereby providing a passwordless login experience to the users
-
End-to-end security
-
Easy to use management tools allow users to manage their own cards/tokens and certificates
-
Easy deployment supported with integration for Web applications and Windows logon
-
Quick processing of authentication requests
-
USB PKI Token agnostic – Supports token device from multiple vendors
-
Supports certificates from other CAs
-
Single authenticator device with multiple use cases - secure access, data encryption and digital signing
-
Reduced IT help desk calls for a password reset
-
Better visibility, tracking, and control of applications by the IT team.
Platform Benefits:
To know more about our product and how it can benefit your business, please contact us.