CyLock MFA for ADFS
AD / LDAP Federation Services (ADFS) serves as a centralized and flexible solution for managing user identities, access controls, seamless integration with existing AD / LDAP environments streamlining authentication processes, and enabling single sign-on (SSO) capabilities across multiple applications. Relying solely on generic password-based authentication in an ADFS implementation can pose significant security vulnerabilities. Passwords are prone to various attacks, including brute force, phishing, and credential reuse, potentially leading to unauthorized access to applications and sensitive data.
To mitigate these vulnerabilities, organizations can enable additional security measures by implementing CyLock MFA along with strong password policies, account lockout mechanisms, session management controls, and regular security assessments.
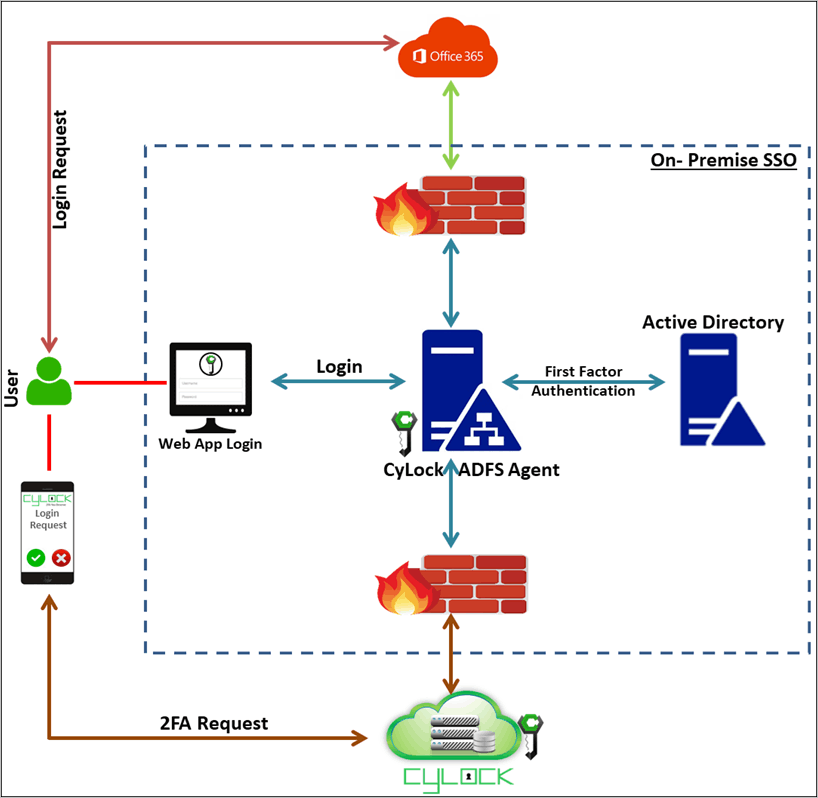
CyLock MFA provides a customized ADFS agent that can be installed in an ADFS server in the on-premise network of the organization. This agent can then act as an Identity Provider and allow web applications to authenticate against AD / LDAP along with MFA while supporting modern authentication protocols like SAML 2.0, OAuth 2.0 and OpenID Connect.
Authentication Options
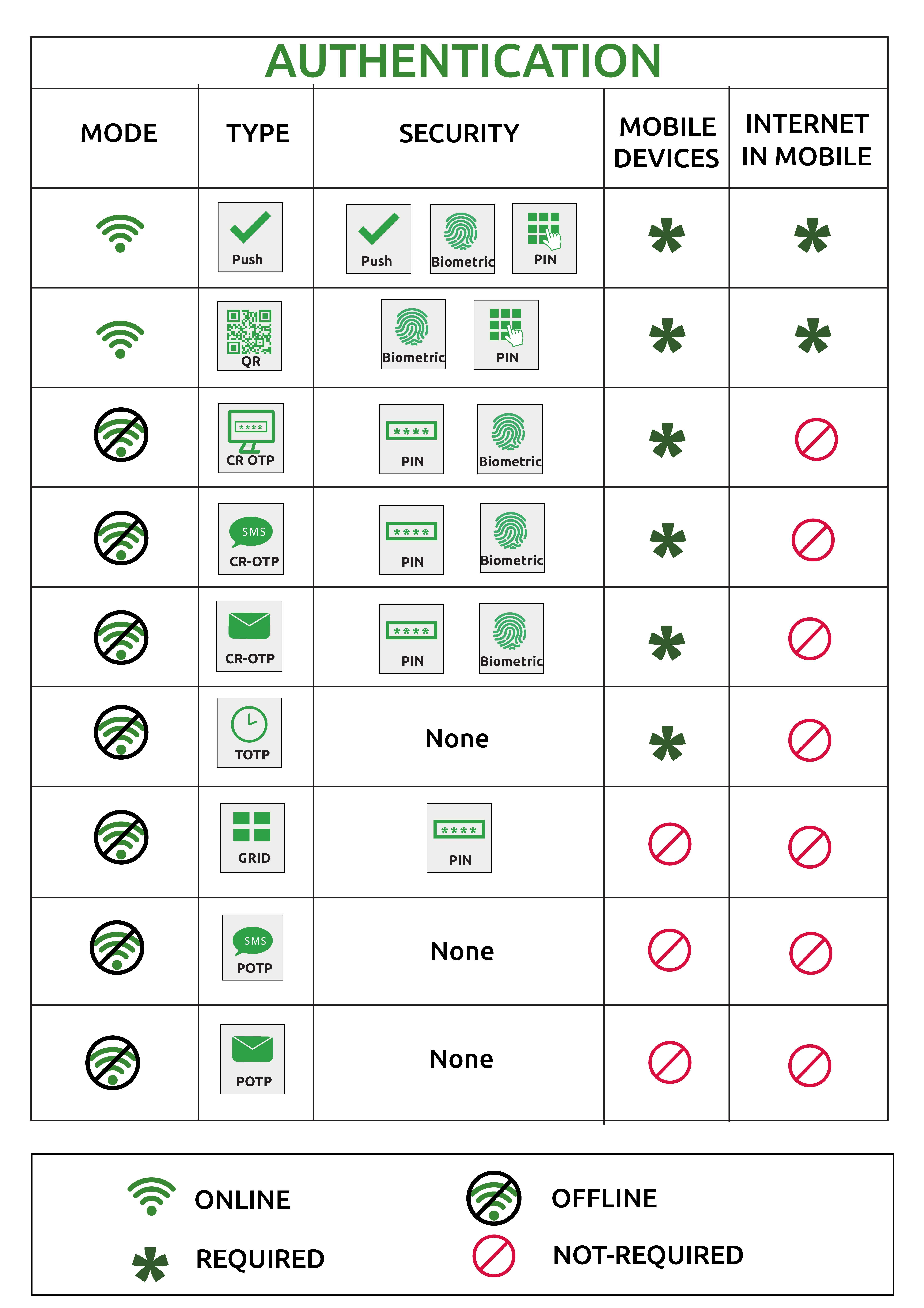
In addition to implementing robust password policies, organizations can enhance the security of web application login process by enabling Multi-Factor Authentication (MFA). MFA adds an extra layer of security, mitigating the risk of cyber-attacks and bolstering protection for enterprise identities and data. The table below outlines the authentication types and security options available during Web application login either through ADFS agent.
Benefits of enabling CyLock MFA for ADFS
Defence against Credential Theft: Enabling MFA in ADFS adds an extra layer of protection, requiring attackers to overcome additional authentication factors beyond just username and password. This significantly reduces the likelihood of successful credential theft and unauthorized access to internal and external federated applications.
Protection against SSO Risks: While Single Sign-On (SSO) streamlines the authentication process for users, it also presents risks, particularly if compromised credentials grant access to multiple applications. Enabling MFA in in SSO implementation using ADFS mitigates this risk by requiring additional verification factors for each authentication attempt, reducing the impact of compromised credentials on SSO-enabled environments.
Strengthened Access Controls: MFA in ADFS strengthens access controls by providing a more robust authentication mechanism than traditional password-based systems alone. By requiring multiple factors for authentication, including something the user knows (password) and something they possess (e.g., mobile device), organizations can implement a stronger security posture and better protect against unauthorized access to sensitive resources.
Increased Visibility and Auditing: Enabling MFA in ADFS enhances visibility into authentication events and provides additional auditing capabilities. Organizations can track and monitor MFA usage, including successful and failed authentication attempts, helping detect and respond to suspicious activities or security incidents more effectively. This increased visibility improves overall security posture and supports compliance efforts by providing detailed audit trails of authentication activities.
Conclusion
In summary, enabling Multi-Factor Authentication (MFA) within an AD / LDAP Federation Services (ADFS) implementation provides targeted benefits that address the vulnerabilities associated with password-based systems and Single Sign-On (SSO) without MFA.